Integration of VPC Flow (Network Traffic) Logs to CloudWatch for Monitoring!
In this Article We have been going to Configure VPC Flow Logs to Send Logs to CloudWatch for monitoring network traffic to VPC and Resources.
Here is the Diagram Which we will follow for whole configuration steps:

Before going forward, we first discuss and define what is VPC Flow Log, CloudWatch and then we will go with Integration steps.
What is VPC Flow Log?
Amazon VPC Flow Logs enable us to capture information about the network traffic moving to and from network interfaces within our VPC (Virtual Private Cloud). We can use VPC Flow Logs as a centralized, single source of information to monitor different network aspects of VPC. So, in other words we can detect remote logins like SSH, RDP or other network traffic going to or from VPC.
What is CloudWatch?
Amazon CloudWatch is a service used for monitoring and observing resources in real-time. CloudWatch collects monitoring and operational data in the form of logs, metrics, and events, providing its users with an aggregated view of AWS resources, applications, and services that run on AWS.
Now we will Proceed with Integration Steps:
Step 1: VPC Creation
First, we will go with VPC Creation in AWS for which we implement Flow Log service.




Now we have created the VPC, we will procced with network configuration by creating subnets in these ranges as follows:
Public Subnet: 12.0.1.0/24
Private Subnet: 12.0.2.0/24
So now we will create these subnets as follows.






Now we will proceed with Internet Gateway, so basically internet gateway is setting or configuration which enable internet communication with our VPC subnets we have created in above step.
Step 2: Internet Gateway Creation


We have created internet gateway then we will proceed with the VPC attachment as we have to enable internet access to our VPC through this gateway.


We have attached our VPC created in first step so now, we will proceed with routing table creation for our VPC.
- Public Routing Table
- Private Routing Table



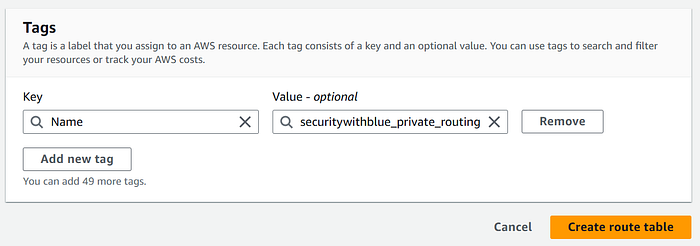
Now we have created public and private routing tables so we associate public subnet with public route table and private route table with private subnet.
Click on Public Route Table ID and associate public subnet with it.



Now same for private route table too.



Now we have associate route tables to respective subnets, in next step we will proceed with attaching routes to public routing table to which traffic is allow to our public subnet as we are not going to attach any route to private subnet as this subnet is not for public.
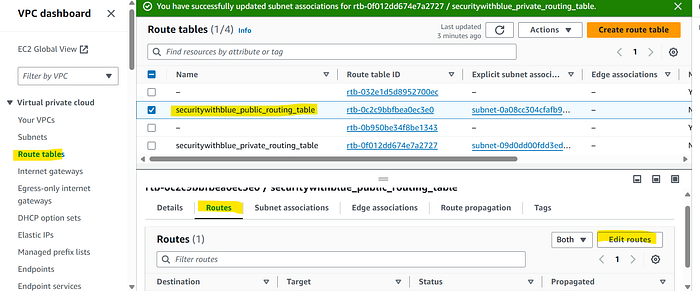
We will attach internet gateway we have created in above steps.

Step 3: EC2 Instance Creation in VPC
Now we will go with creation of EC2 Instance in VPC for which we configure Flow Log and CloudWatch to monitor.

There is no instance running before so we will create as follows.


I have selected the Ubuntu image for my EC2 Instance.

I already have private key you can create your own key for accessing your EC2 Instance.

For Network Setting edit settings and give the VPC and Public Subnet and add security group according to your requirements. I will be going to add ICMP-IPv4.

For ICMP i will add security group.


We can specify the source type according to your own requirements.

Step 4: VPC Flow Log Group Creation
We will create log group to watch specific logs related to VPC as follows:




Step 5: IAM Role Creation
Now we will create IAM Role and attach policies to accessing Logs.



{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principle": {
"Service": "vpc-flow-logs.amazonaws.com"
},
"Action": "sts:AssumeRole"
"Resource": "*"
}
]
}


Now we will create Policies to attach with Role.

{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents",
"logs:DescribeLogGroups",
"logs:DescribeLogStreams"
],
"Effect": "Allow",
"Resource": "*"
}
]
}




Step 6: VPC Attachment with Log Group
Now we will proceed with VPC attachment with log group to send logs to group in CloudWatch.

Select VPC ID and then configure Flow Log.






Now we will check Whether this Flow Created in CloudWatch or not as follows:
Select the Log Group

So, we can see that stream is created for logs with elastic network interface.


We can see in above picture that network logs are coming into log group.
Now we will test logs with pinging EC2 instance to Google 8.8.8.8 IP in public subnet located in VPC and check whether log created or not.


Now we can see that logs are created in log group:

Conclusion:
VPC flow logs with CloudWatch offer a quick and easy insight into network traffic within the VPC. It can be used by the security team to detect and respond to network threats as they occur. Flow Log will provide visibility to the Network and Security Teams to enhance troubleshooting efforts as well as detection of suspicious capabilities.
